What Is A Data Leak Dt Leks & Breches Protecting Your Compny
Not every sensitive data type listed in the report always has a corresponding recommendation. If you are logging in with your personal google account and choose to provide feedback, human reviewers may review your queries, uploads, and the model's responses to troubleshoot, address abuse or make improvements. Official google one help center where you can find tips and tutorials on using google one and other answers to frequently asked questions.
What is Data Leakage? How Do You Prevent It?
You can check for data on the dark web that might be associated with your email address or other info you add to your monitoring profile. We value your privacy and never use your personal data to train notebooklm. Breach results can contain information like:
Any information found in the breach results is displayed in redacted form to maintain data privacy.
This help content & information general help center experience. This help content & information general help center experience. We check for password and username combinations exposed through a wide variety of data breaches, but the list of data breaches we check may be incomplete. Our list includes sources such as:
For information on how google checks if your password has been compromised, see this information on how password protection works. What to scan for—matches predefined data type (recommended) select data type—several data types, including social security number, driver's license number, and united states passport number. The confidence threshold for the condition. This is an extra measure used to determine whether messages trigger the

Password leak detection provides users with alerts when any potentially compromised password use is detected.
This article is intended for administrators and end users who want to learn about what data is collected by password leak detection and how it’s processed by google. Turn warn you if a password was compromised in a data breach on or off. This feature is only available if the safe browsing option is turned on. Dismiss notifications for specific sites:
While some use the terms data breach and leak interchangeably, the two words stand for different incidents. The main distinction between a data leak and breach is: The terms data breach and data leak are often used interchangeably,but that's incorrect as they're two seperate categories of data compromise. A data breach is when sensitive data is accessed and compromised in a successful attack.

A data leak is the exposure of sensitive data that could be used to make future data breaches happen faster.
A data leak differs from a data breach in that a leak is often accidental and caused by poor data security practices and systems. In contrast, a breach is typically the result of a targeted cyberattack by cybercriminals. Once a leak occurs, it exposes sensitive information, making organizations vulnerable to exploitation. Data leak meaning and definition.
A data leak refers to the accidental exposure of sensitive information, whether physically or on the internet. This might include situations where a device is lost or stolen, or when a company uses insecure data storage. A data leak is a security incident where confidential, protected or sensitive data is released to an environment where the data is not meant to exist. Data leaks can result from various reasons, such as system vulnerabilities, improper disposal of data, operational errors, or even malicious insider threats.
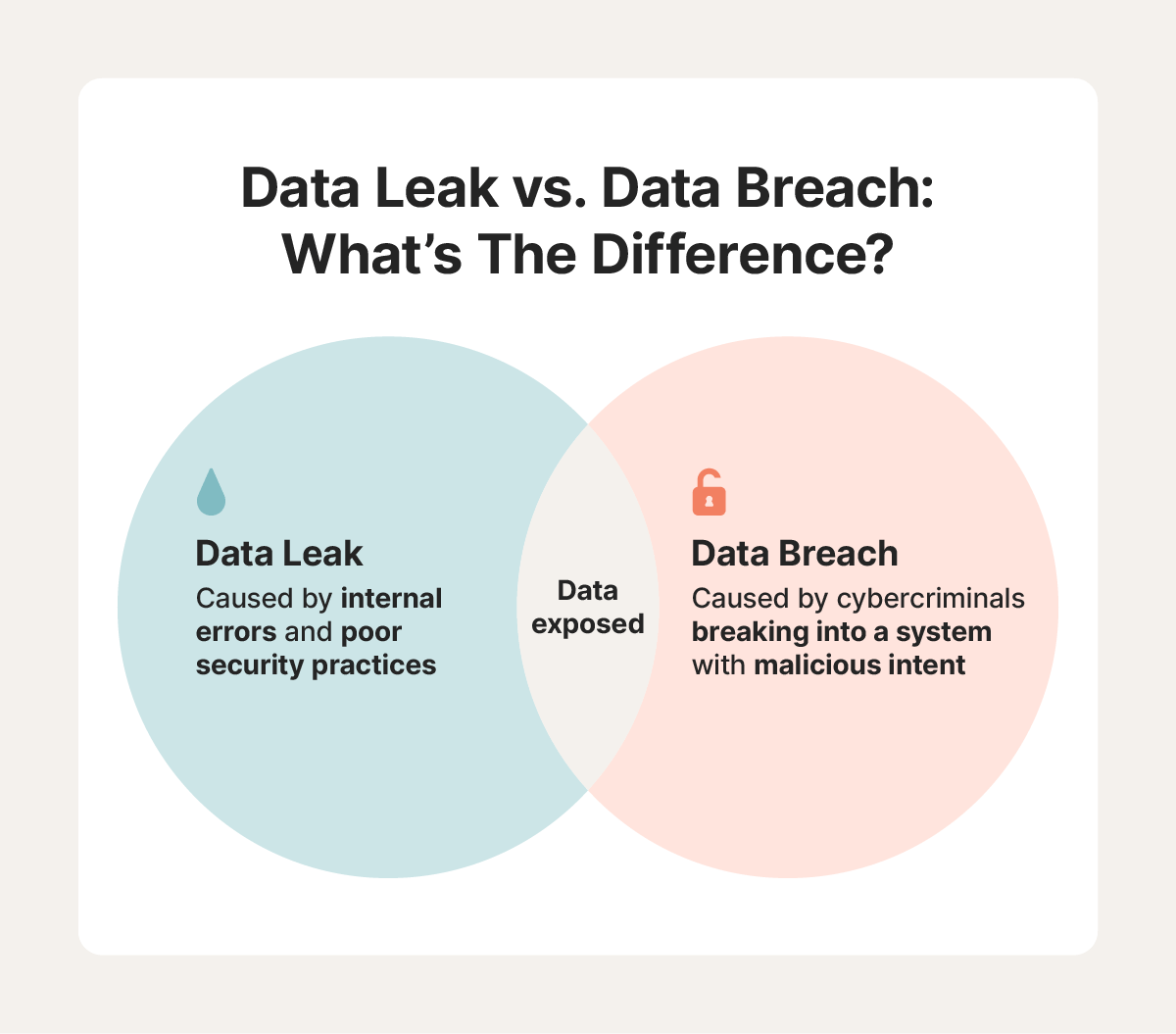
The difference between these two terms is small but important when taking actions to secure the data in question or when reporting on the incident later.
A breach is an incident where data has been unintentionally exposed to the public. Using the 1password password manager helps you ensure all your passwords are strong and unique such that a breach of one service doesn't put your other services at risk. A data leak is the accidental release or exposure of sensitive information due to internal errors or negligence. While a data breach is intentional, a data leak is
People often use the terms data leak and data breach interchangeably; However, they aren’t the same. Although both incidents involve the exposure of confidential data to unauthorized entities, the cause of the revelation differs. As per data leak meaning, it happens when sensitive data is unknowingly and unintentionally exposed to the public
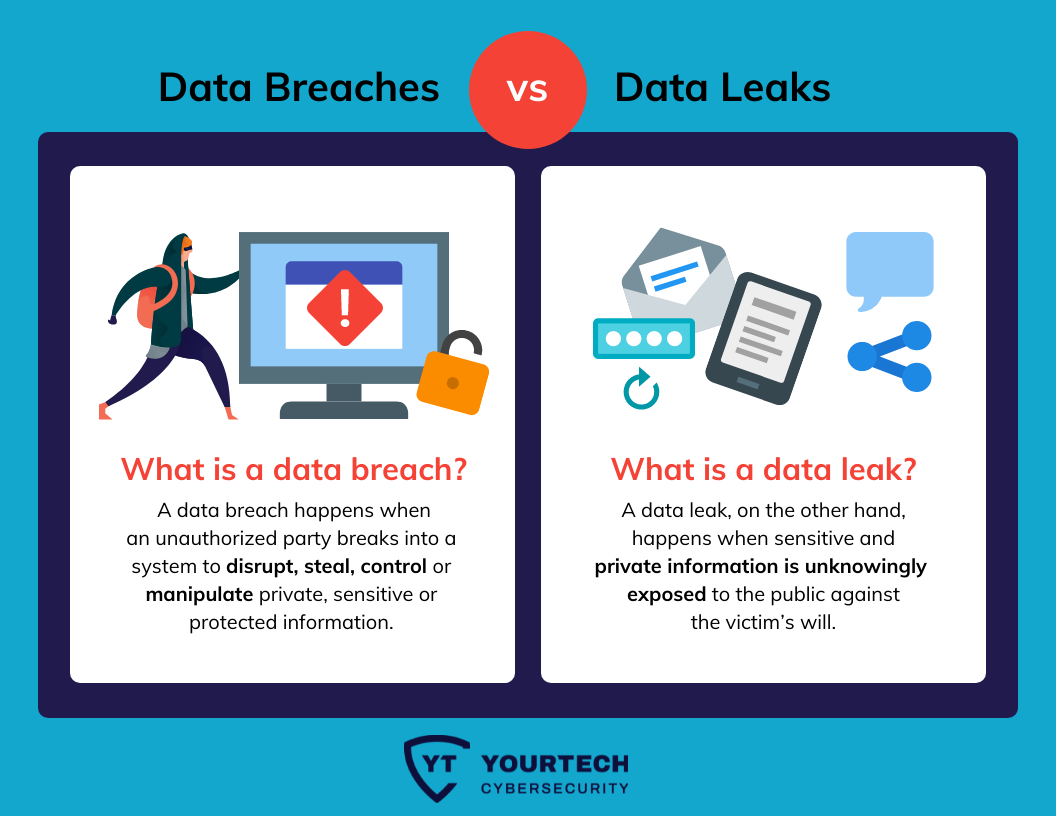
A data leak is the unplanned or unauthorized release of data outside of where it’s supposed to be in an organization.
This can mean that payroll data is leaked outside of the accounting department. Or, it can mean that your customer list is exposed to the public through an oversight or due to the intentional actions of a disgruntled employee. Data leaks can also occur due to software misconfiguration facilitating malicious access to secret information. A good example was the major microsoft power app data leak in 2021.
Data leakage and data loss are often used interchangeably, but they differ. The causes of data loss vs. Data leaks aren’t the same, either Password in data leak notification i received a notification on my iphone x about half an hour ago to say my password had appeared in a data leak.
It listed the sites/passwords i needed to change.
It listed the sites/passwords i needed to change. While data leaks and data breaches are similar (and the terms are often used interchangeably), the core difference is that a data breach describes when an attack results in a threat actor accessing sensitive data, whereas a data leak describes the accidental exposure of sensitive data. A data leak can simply be the disclosure of data to a third party from poor security policies or storage misconfigurations. In most scenarios, a data leak is accidental, while a data breach is malicious and intentional.
Not every sensitive data type listed in the report always has a corresponding recommendation. Official google one help center where you can find tips and tutorials on using google one and other answers to frequently asked questions. You can check for data on the dark web that might be associated with your email address or other info you add to your monitoring profile. Breach results can contain information like:
Any information found in the breach results is displayed in redacted form to maintain data privacy.
This help content & information general help center experience. This help content & information general help center experience. We check for password and username combinations exposed through a wide variety of data breaches, but the list of data breaches we check may be incomplete. Our list includes sources such as:
For information on how google checks if your password has been compromised, see this information on how password protection works. What to scan for—matches predefined data type (recommended) select data type—several data types, including social security number, driver's license number, and united states passport number. The confidence threshold for the condition. This is an extra measure used to determine whether messages trigger the
Password leak detection provides users with alerts when any potentially compromised password use is detected.
This article is intended for administrators and end users who want to learn about what data is collected by password leak detection and how it’s processed by google.